A website has published a real-time map of cyber attacks as they happen. First of all, it's fascinating to watch what's going on on line. As you sit and stare at it, every so often you'll see a mass of attacks all directed at one location, perhaps coming from one location or from all over the world. Like this:
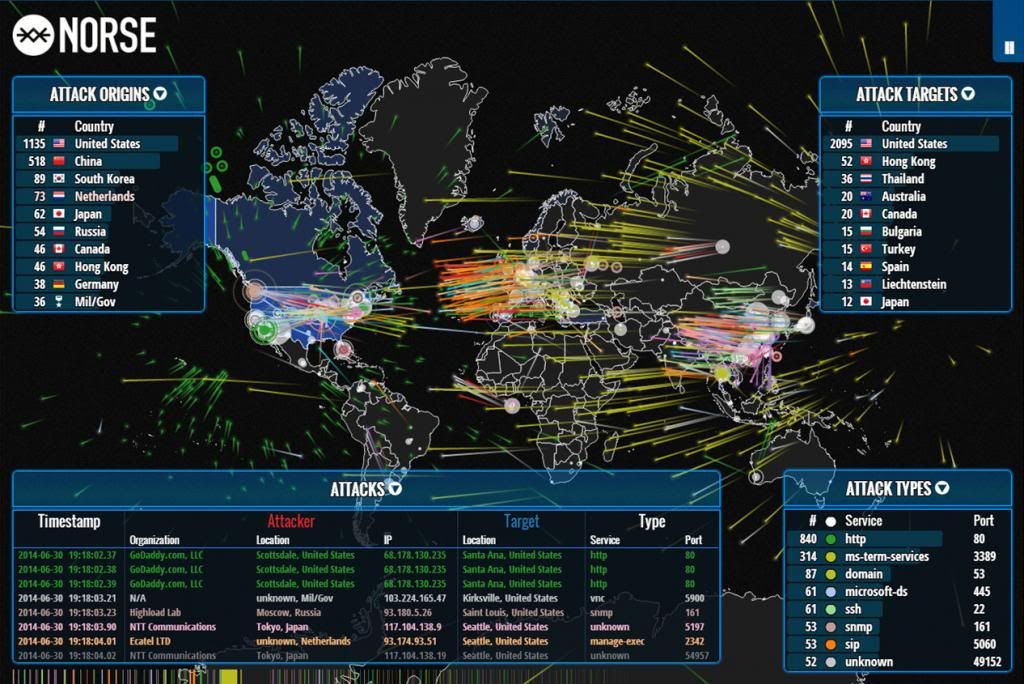
It usually looks more like this:
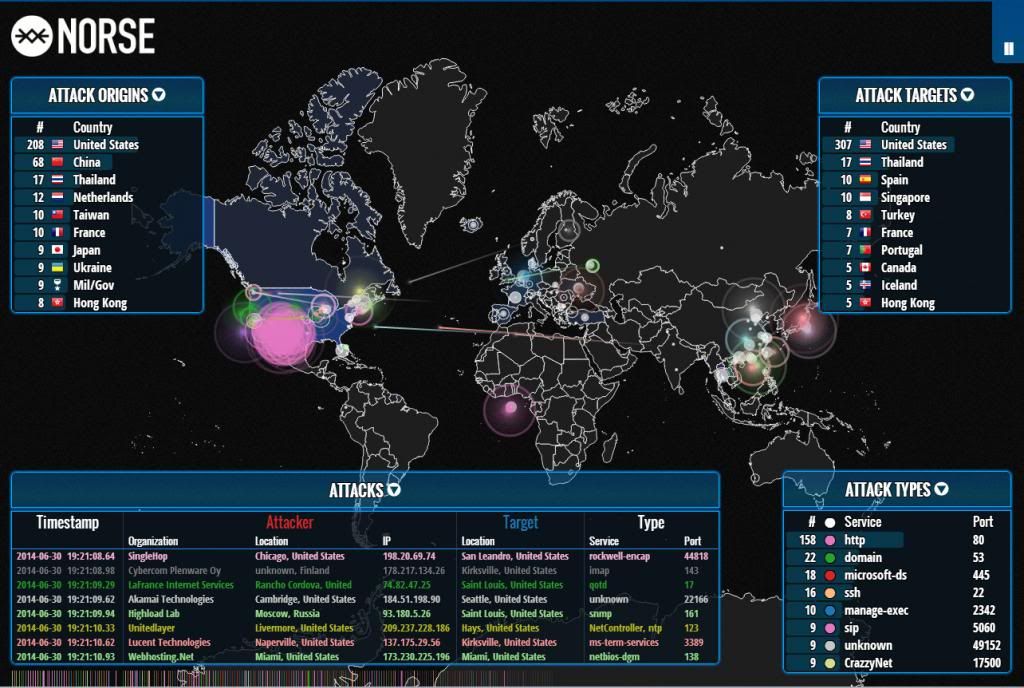
I have to wonder, though, how does this website get the information it's displaying? Or are they just making it up?

It usually looks more like this:

I have to wonder, though, how does this website get the information it's displaying? Or are they just making it up?


